It must consist of:
1. 5 source annotated bibliography
2. Summary or Abstract containing at least 750 words.
It must consist of:
1. 5 source annotated bibliography
2. Summary or Abstract containing at least 750 words.
“A picture is worth a thousand words” may be a lovely cliché, but it’s exactly the wrong way to view visualization. For this week’s discussion question, please view the Periodic Table of Visualization at the following link (http://www.visual-literacy.org/periodic_table/periodic_table.html). Choose one Data Visualization and one Compound Visualization by placing your mouse cursor over each option. Provide your classmates with a brief description of your choices and explain why you made your choices. Also, describe what advantages do your choices have over the others.
Strict APA format
2 pages
At least 2 scholarly references.
Your boss wants you to draft a two- to three-page vulnerability process and assessment memorandum addressing the main points of a VM process for Mercury USA. You will cover the main elements of a vulnerability management process, tailored to Mercury USA’s business in the transportation sector, evaluate the OpenVAS scanning tool, and provide recommendations for mitigating the vulnerabilities found within the OpenVAS report.
The third-party pen tester used the free tool Open Vulnerability Assessment Scanner (OpenVAS) to scan Mercury USA’s network. Review the report from the OpenVAS Scan.
As you review the scan, consider some important points from Remediation:
A three-tier web application architecture has been generically defined as the presentation, business logic, and data storage tiers. However, Amazon Web Services defines the three-tier web application architecture as the web, application, and storage/database tiers.
Write a paper comparing the generic three-tier web application architecture to that applied by Amazon Web Services.
Apply APA Edition 6 formatting.
Use at least three properly documented references (do NOT use wikis).
Correctly cite your references using APA Edition 6 formatting.Your paper should be at least 500 words in length using good grammar.
DEFINITION: a brief definition of the key term followed by the APA reference for the term; this does not count in the word requirement.
SUMMARY: Summarize the article in your own words- this should be in the 150-200 word range. Be sure to note the article’s author, note their credentials and why we should put any weight behind his/her opinions, research or findings regarding the key term.
ANALYSIS: Using 300-350 words, write a brief analysis, in your own words of how the article relates to the selected chapter Key Term. An analysis is not rehashing what was already stated in the article, but the opportunity for you to add value by sharing your experiences, thoughts and opinions. This is the most important part of the assignment.
REFERENCES: All references must be listed at the bottom of the submission–in APA format and only use journal articles
Automation testing is an important task that will help you reduce the time it takes to execute a test case. In this assignment, you will install a trial version of an automation testing tool and then create automation test cases.
The automation testing process includes the following stages:
Please follow the step-by-step instructions and screenshots below to install the tool (Micro Focus, 2018):

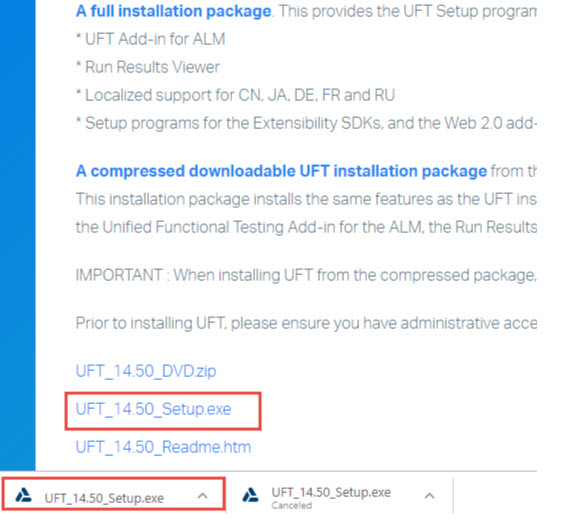
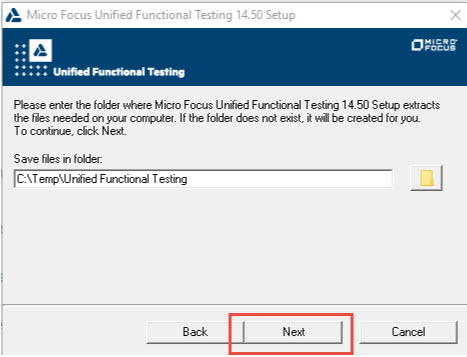
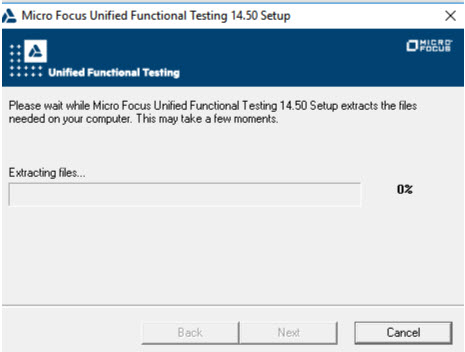
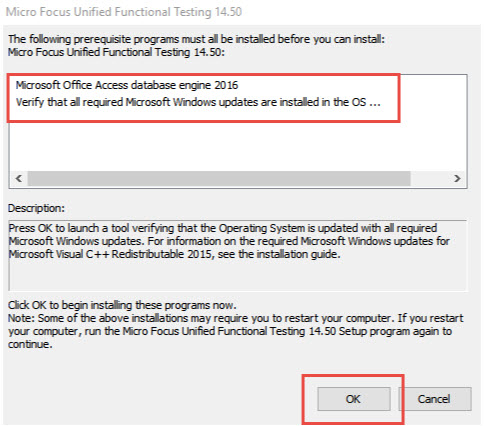
You can also use this PDF file for installation help.
You need to create at least 4–5 automation test cases using either Sample MyFlight or the Calculator application.
Submit the following in a .zip file:
Using a Microsoft Word document, please discuss the case involving the United States of America versus Ross Ulbrecht. Please include what took place at the United States Supreme Court.
2. The minimum word count shall be not less than 500 words in APA format.
Industry experts believe blockchain is a technology that has the potential to affect the business of most IT professionals in the next five years. Pick an industry you feel will be most affected by blockchain and how blockchain may be used in that industry. As an IT manager, how would you embrace blockchain? For instance, how would training occur for your team, what strategies might you use, what security methods may you recommend be used?Your paper should meet the following requirements:
Write a Software Reference Architecture document for a fictitious University information technology department. This Software Reference Architecture should include at least one software framework (e.g. Spring, struct, Hibernate). You can assume the data storage is part of software because it normally uses a database.
Attached is the full description and requirement and rubric for this project.
Part 1: Hypervisors
Review case 8-3 and 8-4. Select one of the two cases from chapter 8 and complete the written exercise.
Case 8-3 Hyper-V
Review case 8-3 and complete the exercise. Provide a minimum of 2 references to support your writing.
OR
Case 8-4 VmWare
Review case 8-3 and complete the exercise. Provide a minimum of 2 references to support your writing.
Part 2: Cloud Security
Chapter 9 lists several common security threats to cloud-based environments. Analyze 3 types of cloud security threats and describe methods to mitigate the risks. Compare and contrast the difference between these security threats in a data center/on site versus from the cloud. Provide a minimum of 3 references to support your findings.
Requirements:
Total page count should be a minimum of 3 pages.
Make sure to cite any content provided from your sources.
Minimum number of references for the assignment is 5.