-Explain Normalization and De-Normalization.
-What are the different types of Normalization? -What is BCNF?
-What is SQL?
-How many SQL statements are used? Define them.
online discussion bhar
Do you feel that countries and companies need explicit strategies for technology development, given the tremendous amount of largely spontaneous creativity that occurs today, often in areas where new technologies are not expected to exert a great influence. Why or why not?
Cyber security
I need help answering some questions .It is about analyzing network traffic using network analysis tool
incident response wk3 discusion
Considering the enterprise environment, detail two methodologies for obtaining buy-in from an organization’s executive team in support of network monitoring.
Participate in the weekly discussion. Post your initial 250 word minimum response to the discussion question and reply with a substantial contribution to the posts of other students.
Note: You will not see the work of other students until you make your DQ post.
Remember to use APA citations and references if you refer to information such as statistics or information you used in your response from other sources. DO NOT directly copy from a website or other source and paste. In this course I will only accept paraphrasing not direct quotation on all work.
cs
Part I: Complete Your Original Response to the Main Topic
The requirement of this activity for this module is for every student to solve one programming problem from the book, and post the source code in the discussion board for further analysis and discussion. In order to have more diversity of problems from the chapter, each student will select a problem number using the process described below.
Selecting the Problem Number to Use
Consider the following rules in calculating the problem number to solve:
- Find the absolute value of the difference between 12 and the remainder of the division of your student ID by 12.
Posting the Solution
Once you determine the problem number, complete the solution to that problem. When you are satisfied with your solution, click the Reply link below to post in this discussion forum.
- In the first line of your post, your should add the chapter number, problem number, and page number of your problem.
- Your posting must include the source code along with explanations of how you have solved the problem.
Business Stratergy
1) 350 words – Why is it critical for company managers to have a clear strategic vision regarding their organization?
2) 1 reply of 150 words
Informatics
O
From the moment you wake, you are in fact a data-generation machine. Each use of your phone, every transaction you make using a debit or credit card, even your entrance to your place of work, creates data. It begs the question: How much data do you generate each day? Many studies have been conducted on this, and the numbers are staggering: Estimates suggest that nearly 1 million bytes of data are generated every second for every person on earth.
Business Intelligence 12
Watch the following two videos: https://www.
youtube.com/watch?v=GHc63Xgc0-8 and https://
www.youtube.com/watch?v=ggN8wCWSIx4 for a
different view on impact of AI on future jobs. What are
your takeaways from these videos? What is the more
likely scenario in your view? How can you prepare for
the day when humans indeed may not need to apply
for many jobs?
Constraint satisfaction problem
## Problem 2 – CSP
Consider the following constraint satisfaction problem. A linear graph has nodes of the following colors:
– Red
– Yellow
– Green
– Blue
– Violet
Each node has a domain of {1, 2, …, 9}.
Each node type has the following constraints on its value:
– Red – No contraints
– Yellow – equals the rightmost digit of of the product of all its neighbors
– Green – equals the rightmost digit of the sum of all its neighbors
– Blue – equals the leftmost digit of the sum of all its neighbors
– Violet – equals the leftmost digit of the product of all of its neighbors
As a reminder here is the pseudo code for the Min-Conflicts search algorithm:
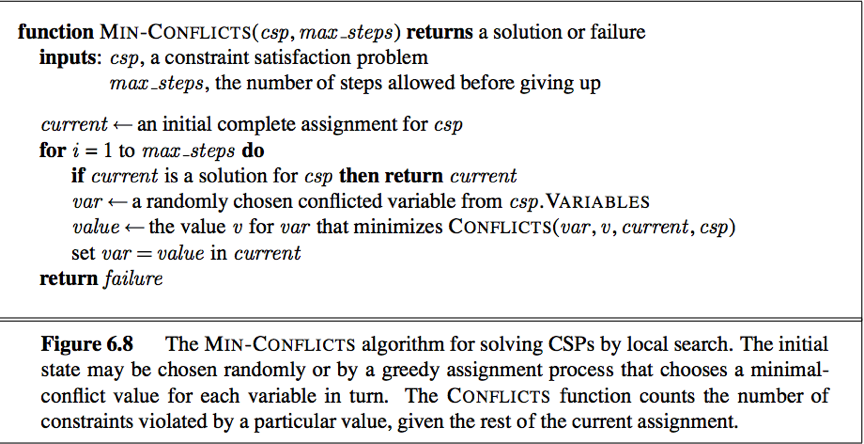
**Notes:**
– It’s possible that you won’t converge to a solution in a single run. Try a few runs to see if you get to a solution.
– The example is to show you what a problem looks like, we will test/grade your program on different examples
Complete the function *solve_csp* defined below. You may find some helper functions useful.
Assignment
Select any example of a visualisation or infographic, maybe your own work or that of others. The task is to undertake a deep, detailed ‘forensic’ like assessment of the design choices made across each of the five layers of the chosen visualisation’s anatomy. In each case your assessment is only concerned with one design layer at a time.
For this task, take a close look at the data representation choices:
- Start by identifying all the charts and their types
- How suitable do you think the chart type choice(s) are to display the data? If they are not, what do you think they should have been?
- Are the marks and, especially, the attributes appropriately assigned and accurately portrayed?
- Go through the set of ‘Influencing factors’ from the latter section of the book’s chapter to help shape your assessment and to possibly inform how you might tackle this design layer differently
- Are there any data values/statistics presented in table/raw form that maybe could have benefited from a more visual representation?
Assignment Link: http://book.visualisingdata.com/chapter/chapter-6
Assignment Requirements: At least 500 words in length
References: At least three peer-reviewed, scholarly journal references.