Discuss the best presentation that you have ever seen. What made it different from the rest of the presentations you have seen? Why did it have such an impact on you? How can you begin to incorporate some of the items mentioned in your next presentations?
Discussion
Q:What are the advantages and disadvantages of a Private Cloud vs. a Public Cloud delivery model? When would you implement each and why?
Application Security Practical Connection Assignment- Subject Cyber Security _ Recent articles
Prepare a report to address all aspects of the assignment. This report should be no less than 5 pages of content. You need to include outside sources and properly cite and reference your sources. You must have at least 10 references, 5 of which must be scholarly peer-reviewed articles. In addition to the 10 pages of content, you will want a title page and a reference sheet. This report needs to be in proper APA format.
Paper Sections
The following sections should be outlined as Headers in the paper.
Introduction, thesis statement, overview, purpose
Background, discuss history of topic
Discussion, identify benefits, obstacles, innovations
Conclusion, summarize the overall study, lessons learned
References, minimum three references with citations in the body
All written reports should be submitted in MS Word. The paper submission will use SafeAssign. Please ensure to use the proper Author, YYYY APA citations with any outside content brought into the paper.
cookies
Write a C++ program that asks the user for the number girl scouts in their troop and the number of weeks they sold boxes of cookies.The program should collect the following information using nested for loops:•The first name of each girl scout.•The number of boxes of cookies sold each week by each girl scout.The program should calculate and display the following information:•The total boxes of cookies sold by each girl scout.•The total boxes of cookies sold by the entire troop.•The average boxes sold per week by the troop.•The name of the girl scout who sold the most cookies.Cookie Counter ProgramLab 7 –More LoopingSample Program Output on the next page.Make sure to include the following input validation:•Validate that the number of girl scouts is greater than zero.•Validate that the number of weeks sold is greater than zero.•Display an error message if either condition above occurs.f
Presentation
Presentation 20 slides.
How Virtual reality will influence the world in the next five years?
**Including note**
Design and implement Java program as follows: 1) Implement converter class hierarchy as follows: a
Design and implement Java program as follows: 1) Implement converter class hierarchy as follows: a
Design and implement Java program as follows: 1) Implement converter class hierarchy as follows: a. Converter class which includes: • Private attribute for input of data type double • Default constructor with no parameter which sets input to Double.NaN • Overloaded constructor with input for parameter • Get and set methods for input attribute • Method
This problem has been solved!
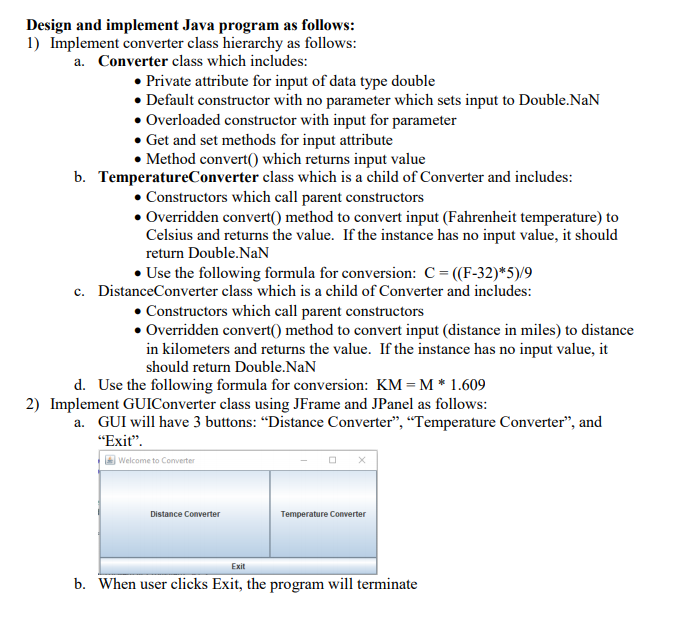
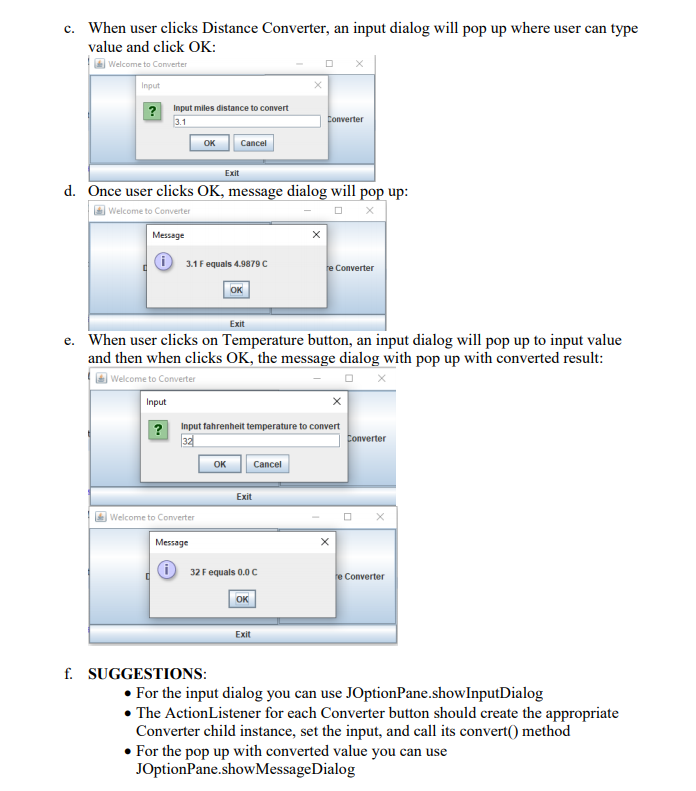
Design and implement Java program as follows: 1) Implement converter class hierarchy as follows: a. Converter class which includes: • Private attribute for input of data type double • Default constructor with no parameter which sets input to Double.NaN • Overloaded constructor with input for parameter • Get and set methods for input attribute • Method convert() which returns input value b. TemperatureConverter class which is a child of Converter and includes: . Constructors which call parent constructors • Overridden convert() method to convert input (Fahrenheit temperature) to Celsius and returns the value. If the instance has no input value, it should return Double.NaN • Use the following formula for conversion: C = ((F-32)*5)/9 c. Distance Converter class which is a child of Converter and includes: • Constructors which call parent constructors • Overridden convert() method to convert input (distance in miles) to distance in kilometers and returns the value. If the instance has no input value, it should return Double.NaN d. Use the following formula for conversion: KM=M* 1.609 2) Implement GUIConverter class using JFrame and JPanel as follows: a. GUI will have 3 buttons: “Distance Converter”, “Temperature Converter”, and “Exit”. Welcome to Converter Distance Converter Temperature Converter Exit b. When user clicks Exit, the program will terminate c. When user clicks Distance Converter, an input dialog will pop up where user can type value and click OK: Welcome to Converter Input ? input miles distance to convert 3.1 Converter OK Cancel Exit d. Once user clicks OK, message dialog will pop up: Welcome to Converter Message х 03.1 F equals 4.9879c re Converter OK Exit e. When user clicks on Temperature button, an input dialog will pop up to input value and then when clicks OK, the message dialog with pop up with converted result: Welcome to Converter Input ? Input fahrenheit temperature to convert 32 Converter OK Cancel Exit Welcome to Converter Message X 0 32 F equals 0.0C he Converter OK Exit f. SUGGESTIONS: • For the input dialog you can use JOptionPane.showInputDialog • The ActionListener for each Converter button should create the appropriate Converter child instance, set the input, and call its convert() method • For the pop up with converted value you can use JOptionPane.showMessageDialog Style and Documentation: Make sure your Java program is using the recommended style such as: Javadoc comment up front with your name as author, date, and brief purpose of the program Comments for variables and blocks of code to describe major functionality Meaningful variable names and prompts • Class names are written in upper CamelCase • Constants are written in All Capitals • Use proper spacing and empty lines to make code human readable Capture execution: You should capture and label screen captures associated with compiling your code, and running the a passing and failing scenario for each functionality
Research Paper
Download The Attachments and Message Me Please for Detailed Instructions
Exp19_Excel_Ch05_HOEAssessment_Fine_Art
#Exp19_Excel_Ch05_HOEAssessment_Fine_Art
#Exp19 Excel Ch05 HOEAssessment Fine Art
Project Description:
You are an analyst for a fine art dealer. Customers are especially fond of James C. Christensen’s art. You prepared a list of his artwork: Title (title of each piece of art), Type (the medium, such as Limited Edition Print or Anniversary Edition Canvas), Edition Size (how many copies were produced for purchase), Release date (the month and year the art was released), Issue Price (the original retail price when the art was released), and Est. Value (the estimated current market value). Studying the data will help you discuss value trends with art collectors
Start Excel. Download and open the file named Exp19_Excel_Ch05_HOEAssessment_FineArt.xlsx. Grader has automatically added your last name to the beginning of the filename.
Before using the Subtotal command, the data must be sorted by categories.
On the Subtotals worksheet, perform a three-level sort by Status, then by Type, and finally by Title, all in alphabetical order.
You want to subtotal data to identify the highest issue prices, estimated values, and percentage change by the Status category and the Type of art work.
Use the Subtotals feature to insert subtotal rows by Status to identify the highest (max) Issue Price, Est. Value, and Change. Then add a second-level subtotal by Type using the same function and columns.
You want to apply an outline so that you can collapse values used for the formula in column F. Then you will collapse the subtotaled rows.
Apply an auto outline and click the collapse button above column F. Collapse the data by displaying only the subtotals and grand total rows. Set a print area for the range B1:F48.
A PivotTable can give additional perspective to data. You will use the Art worksheet to create a recommended PivotTable.
Use the Art worksheet to create the recommended PivotTable called Sum of Issue Price by Type on a new worksheet named Sold Out. Mac users create a PivotChart that includes the Status field in the Filters area, the Est. Values field in the Columns area, the Type field in the Rows area, and the Issue Price field in the Values area.
Name the PivotTable Art Type.
Currently, the PivotTable contains the Issue Price field. You will add the Est. Value field to compare the difference between total value of the art based on issue price and estimated value today.
Add the Est. Value field below the Sum of Issue Price in the Values area.
You want to display the average values instead of the sum of the values in each category.
Modify the two Values fields to determine the average Issue Price and average Est. Value by type. Change the custom name to Average Issue Price and Average Est. Value, respectively.
Format the two Values fields with Accounting number type with zero decimal places.
The Summary sheet is designed to display two key averages from the PivotTable on the Summary sheet.
Display the Summary sheet. In cell B2, insert the GETPIVOTDATA function that references cell C4 on the PivotTable in the Sold Out sheet. In cell B3, insert the GETPIVOTDATA function that references cell C9 on the PivotTable in the Sold Out sheet.
Some art is still available, but most art is sold out. You want to create a filter to focus on the sold-out art.
Display the Sold Out sheet. Add the Status field from the field list to the Filters area. Set a filter to display only art that is Sold Out.
Insert a slicer for the Type field, change the slicer height to 2 inches, change the button width to 2 inches, and apply the Light Blue, Slicer Style Dark 5. Cut the slicer and paste it in cell A11.
Note, depending upon the Office version used, the style name may be Slicer Style Dark 1.
Display the Totals sheet. Insert a calculated field named Field1 to determine difference between the two values, Est. Value and Issue Price. Change the custom name to Value Increase.
With the PivotTable on the Totals sheet displayed, change the Sum of Issue Price and Sum of Est. Value fields to show values as percentage of column totals.
With the PivotTable on the Totals sheet displayed, select Light Blue, Pivot Style Medium 6 and display banded rows.
Display the Porcelains sheet. Create a relationship between the PORCELAINS table using the Code field and the CODES table using the Code field.
Create a blank PivotTable from inside the PORCELAINS table. Add this data to the Data Model. Name the worksheet Porcelain Pivot and name the PivotTable Porcelain Values.
Display all tables in the PivotTable Fields List task pane. Add the Description from the CODES table to the Rows area and the Issue and Est. Value fields as Values from the PORCELAIN table. Format the two value fields with Accounting number format with zero decimal places.
Create a clustered column PivotChart from the Porcelain Values PivotTable. Cut the PivotChart and paste it in cell A7.
Add a chart title and type Porcelain Values. Bold the title. Change the value axis maximum bounds to $3,000.
Change the PivotChart height to 2.5 inches and the width to 3.7 inches.
Create a footer on all worksheets (except Art) with your name in the left section, the sheet name code in the center section, and the file name code in the right section.
Ensure that the worksheets are correctly named and placed in the following order in the workbook: Subtotals, Totals, Sold Out, Art, Summary, Porcelain Pivot, Porcelains.
Save and close Exp19_Excel_Ch05_HOEAssessment_FineArt.xlsx. Exit Excel. Submit the file as directed
3rd case study
Read the Closing Case at the end of Chapter 4 just before the End Notes in the Management of Information Security Book. Answer the two initial Discussion Questions.
Discussion Questions
1. If the Enterprise Policy Review Committee is not open to the approach that Mike and Iris want to use for structuring lnfoSec policies into three tiers, how should Mike and Iris proceed?
2. Should the CISO (Iris) be assessing HR policies? Why or why not?
Second under Ethical Decision Making, answer the following:
- Has Mike broken any laws in representing Iris’ policy work as his own?
- Has Mike committed an ethical lapse in doing so, or is he just being inconsiderate
Computer Science Homework
Question 1 — Based upon the current state of the art of robotics applications, which industries are most likely to embrace robotics? Why?
Question 2 — Question 2 — Watch the following two videos: https://www.youtube.com/watch?v=GHc63Xgc0-8 and https://www.youtube.com/watch?v=ggN8wCWSIx4 for a different view on the impact of AI on future jobs. What are your takeaways from these videos? What is the more likely scenario in your view? How can you prepare for the day when humans indeed may not need to apply for many jobs?
Question 3 — Identify applications other than those discussed in this chapter where Pepper is being used for commercial and personal purposes.
Question 4 — Conduct research to identify the most recent developments in self-driving cars.