Section 1 Cisco Binary game
https://learningnetwork.cisco.com/s/binary-game
Provide a screen shot of you achieving level 4.
https://learningnetwork.cisco.com/s/binary-game
Provide a screen shot of you achieving level 4.
For this assignment, please use the Cyberactive Blackboard application in use at Bellevue University.
1. Create 15 or more User Stories concerning the Blackboard application.
a. NUMBER YOUR USER STORIES!
b. The user for all 15 user stories must be “Student”.
c. You may describe an existing feature of Blackboard, or a feature you wish it had.
d. For each User Story create at least two Acceptance Criteria (a minimum of 30 total Acceptance Criteria).
e. YOU MUST FOLLOW THE PROPER USER STORY FORMAT TO RECEIVE POINTS FOR THIS ASSIGNMENT.
2. Organize your User Stories into a Product Backlog. Assign priorities to each User Story and order them by Priority.
3. Using the Product Backlog, create two Sprint Backlogs that might be suitable for a two-week Sprint each.
a. Assign some or all of your 15 User Stories to each Sprint.
b. Make sure that you assign them in priority order.
User story format:
As a
Case Project 6-2: Setting Up Remote Access for Contractor, Page 251
Scenario: Several new projects are being staffed by outside contractors, who will be working on servers in the contractors’ office, not in the company building, and will have their own VPN server. The contracting company has informed your company that none of its employees will be working weekends. What controls can you set up to minimize contract employees’ access to your network?
Writing Requirements:
1-2 pages
2-3 Scholarly references
APA format, for citations and references
Here is a real world scenario that plays out every day in many organizations.
Please post your thoughts and observations on this scenario. For example, if you were the team leader, what would be your assessment of the intern’s behavior? What should the intern have understood about workplace etiquette? What is the problem with this exchange and what should the intern have done in the beginning?
Watch a Lecture and complete a summary of the lecture.
– Pick one of the following terms for your research: centralization, contingency, decentralization, efficiency, mechanistic, organic, organizational behavior, scientific management, stakeholder, or sustainability.
– The paper should have a definition and Summary( Summary should be a minimum of 200 words)
– Attach minimum 2 references
– Absolutely no plagiarism, attach a plagiarism report with 0% similarity index.
Write a program that does the following in order:
1. Asks the user to enter a name
2. Asks the user to enter a number “x”
3. Asks the user to enter a number “y”
4. Calculates the sum of “x” and “y”
5. Prints out the number for “x”, “y” and “sum”
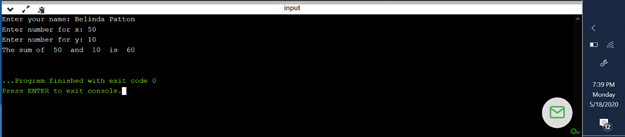
An example of the program input and output is shown below:
Enter your name: Belinda Patton
Enter number x: 50
Enter number y: 10
The sum of 50 and 10 is 60
Do a bit of research on-line. Find a criminal case that involved Digital Forensics.
Using WORD, write an ORIGINAL brief document of 300 words or more describing the case and the how digital forensics were used in the investigation.
Project Deliverable 2: Risk Assessment Outline and Certification Test Matrix Plan
For this deliverable you will generate the Risk Assessment Outline and the Certification Test Matrix Plan based on the results of the Potential Vulnerabilities Report created in Module 1.
Risk Assessment
Using the format in the Howard text on page 279, develop the Risk Assessment Outline. Insert this document as Appendix 2 in the SSP submitted in Module 1.
Certification Text Matrix
Using the format in the Howard text on page 285, create a certification test matrix. Insert this as Appendix 3 in the SSP.
You may find the Threat List helpful in generating these appendices.
Submit this assignment to Canvas no later than the date identified above.
**COMPUTER SCIENCE helper only**
One of the most common uses of client-side JavaScript is to validate form data. When we say “validate” form data, we mean ensuring that the data entered is clean, error free, formatted correctly, and meets certain criterion. The validation of input data is crucial because it ensures that the data is captured in a format that can be used most efficiently. Web designers and developers use client-side JavaScript as one method for validating user-inputted data. The purpose of this project is to build an HTML5 registration form and use JavaScript functions to validate user-inputted data.
Please find attachment for more details – all requirement have to be met no exeception whatsover!